Penetration Testing Services for Cloud, API & Zero Trust Environments
Modern enterprise environments are no longer defined by a clear network perimeter. Cloud platforms, API-driven architectures, and Zero Trust security models have fundamentally changed how systems are built and accessed. While these architectures improve scalability and agility, they also introduce new attack paths that traditional penetration testing approaches fail to detect.
Attackers today focus less on exploiting software vulnerabilities and more on abusing identity, permissions, trust relationships, and business logic. Penetration Testing Services must therefore evolve to validate how real attackers operate in cloud-native, API-centric, and Zero Trust environments. The objective is not just to find vulnerabilities, but to understand how small weaknesses can be chained into full-scale compromise.
Cloud Penetration Testing: Mapping Realistic Attack Paths
Cloud breaches rarely occur due to flaws in cloud provider infrastructure. Instead, attackers exploit misconfigured identities, overly permissive roles, exposed services, and weak trust boundaries. Cloud penetration testing focuses on identifying how an attacker can move from limited access to high-impact compromise by chaining configuration weaknesses.
Rather than treating cloud resources as isolated components, penetration testing evaluates how permissions, services, and network controls interact. This approach reveals escalation paths that are invisible to automated scanning tools.
Key technical areas validated during cloud penetration testing:
- IAM role privilege escalation and trust abuse
- Excessive permissions across cloud services
- Abuse of instance metadata services
- Publicly exposed storage, databases, and admin interfaces
- Cross-account access through misconfigured role assumptions
Cloud Identity and Access Management (IAM) Exploitation
IAM is the most critical control plane in cloud environments. A single over-permissive role or poorly scoped policy can allow attackers to escalate privileges without exploiting any vulnerability. Penetration testing focuses on identifying whether compromised identities can be leveraged to gain broader control over cloud resources.
This includes testing both human and non-human identities, such as service accounts and workload identities, which are often overlooked during security reviews.
IAM-focused attack techniques tested:
- Privilege escalation via policy misconfiguration
- Role chaining across services
- Abuse of wildcard permissions
- Enumeration of unused or forgotten identities
- Credential harvesting from applications and CI/CD systems
Cloud Network Segmentation and Lateral Movement
Although cloud environments are software-defined, lateral movement is still a major risk. Attackers frequently exploit weak segmentation, overly broad firewall rules, and trusted internal services to move between workloads once initial access is gained.
Penetration testing validates whether network boundaries actually prevent unauthorized movement or simply create an illusion of isolation.
Network-level weaknesses tested:
- Insecure security group and firewall configurations
- Over-trusted internal service endpoints
- Misconfigured VPC or virtual network peering
- Flat network architectures within cloud environments
- Insufficient isolation between production and non-production workloads
Container and Kubernetes Penetration Testing
Containerized workloads and Kubernetes clusters introduce an orchestration layer that significantly expands the attack surface. Attackers often target Kubernetes APIs, RBAC configurations, and workload identities rather than individual containers. Penetration testing evaluates whether container isolation and cluster controls prevent privilege escalation and host-level compromise.
Testing focuses on the control plane as much as the workloads themselves, since compromise of Kubernetes often leads to compromise of the entire cloud environment.
Advanced container and Kubernetes attack vectors tested:
- Kubernetes RBAC privilege escalation paths
- Access to kubelet and API server endpoints
- Abuse of mounted service account tokens
- Container escape attempts
- Insecure handling of secrets and configuration data
API Penetration Testing: Authorization Over Exploitation
APIs are the primary interface between modern applications and their users. However, API breaches are rarely caused by injection vulnerabilities. Most successful attacks exploit authorization failures, token misuse, and logic flaws. API penetration testing therefore focuses on understanding how APIs enforce access controls across different users, roles, and workflows.
This type of testing requires manual analysis and attack simulation, as automated tools are unable to understand business context and authorization logic.
Core API security risks validated:
- Broken Object Level Authorization (BOLA)
- Broken Function Level Authorization (BFLA)
- Token scope manipulation and replay attacks
- Insecure token lifecycle management
- Weak enforcement of role-based access
Business Logic Abuse in API-Driven Applications
Business logic vulnerabilities occur when applications enforce security controls inconsistently across workflows. These flaws allow attackers to perform actions that are technically valid but logically unauthorized. Because these attacks do not rely on malformed input or abnormal behavior, they are difficult to detect using traditional security controls.
Penetration testing manually evaluates API workflows to identify whether attackers can manipulate application state to their advantage.
Common logic abuse scenarios tested:
- Workflow bypass through out-of-sequence requests
- Manipulation of pricing, quantity, or limits
- Abuse of refund, credit, or discount mechanisms
- Race condition exploitation
- Multi-step authorization failures
API Abuse and Automation-Based Attacks
APIs are particularly vulnerable to automation-based attacks due to their machine-friendly design. Without proper rate limiting and behavioral controls, attackers can abuse APIs at scale without triggering alerts.
Penetration testing simulates these attack patterns to determine whether APIs can withstand real-world abuse.
Automation and abuse techniques tested:
- Credential stuffing and brute-force attacks
- Enumeration of sensitive data
- Excessive API data extraction
- Abuse of background processing and webhooks
- Denial-of-service via resource exhaustion
Zero Trust Penetration Testing: Validating Assumptions
Zero Trust security models are built on the principle that no identity or device should be trusted by default. However, many Zero Trust implementations still rely on static policies, implicit trust relationships, and overly broad access permissions. Penetration testing validates whether Zero Trust controls actually prevent attackers from moving laterally after identity compromise.
The focus is on breaking trust assumptions rather than bypassing technical controls.
Zero Trust weaknesses commonly tested:
- OAuth and SSO token misuse
- MFA fatigue and bypass scenarios
- Conditional access policy gaps
- Over-trusted service identities
- Weak enforcement of least privilege
Identity-Centric Attacks in Zero Trust Environments
In Zero Trust architectures, identity becomes the primary attack target. Attackers focus on stealing, replaying, or abusing tokens rather than exploiting systems directly. Penetration testing evaluates how identities are issued, validated, and revoked across environments.
This includes testing both user identities and service-to-service authentication mechanisms.
Identity-based attack paths tested:
- Token replay and session hijacking
- Abuse of long-lived access tokens
- Identity federation weaknesses
- Insecure service authentication flows
- Insufficient monitoring of identity behavior
Lateral Movement in Zero Trust Architectures
Despite Zero Trust principles, lateral movement remains possible when services implicitly trust each other or share excessive permissions. Penetration testing simulates attacker movement across identities, workloads, and APIs to determine whether segmentation controls are effective.
This testing reveals whether Zero Trust is implemented as a security strategy or merely as a network design concept.
Lateral movement techniques evaluated:
- Service-to-service authentication abuse
- Token pivoting between workloads
- Exploitation of trusted internal APIs
- Over-permissioned workload identities
- Weak microsegmentation enforcement
Continuous Attack Surface Expansion in Cloud and Zero Trust
Cloud and Zero Trust environments change continuously due to automation, CI/CD pipelines, and infrastructure-as-code deployments. New assets are frequently introduced without proper security validation, creating temporary but highly exploitable exposure windows.
Penetration testing assesses whether organizations can detect and secure these changes before attackers do.
Dynamic exposure risks tested:
- Shadow APIs and undocumented services
- Temporary credentials with excessive privileges
- Insecure CI/CD pipeline integrations
- Misconfigured infrastructure-as-code templates
- Unmonitored external-facing services
How Advanced Penetration Testing Services Reduce Real Risk
Modern Penetration Testing Services focus on validating security assumptions, not just identifying vulnerabilities. By simulating real-world attacker behavior, organizations gain insight into how weaknesses combine to create meaningful risk.
This approach enables security teams to prioritize remediation based on impact rather than vulnerability counts.
Key outcomes delivered by advanced penetration testing:
- Identification of real attack chains
- Improved identity and access control design
- Stronger segmentation and isolation
- Reduced likelihood of large-scale breaches
- Clear, actionable remediation guidance
Compliance Alignment Without Checkbox Testing
Many regulatory frameworks require penetration testing, but compliance-driven testing often lacks depth. Advanced penetration testing aligns with standards such as PCI DSS, ISO 27001, SOC 2, and HIPAA while still focusing on real-world security.
Rather than testing for compliance alone, penetration testing demonstrates whether controls are effective in practice.
Compliance-related validation areas include:
- Scope-aligned testing methodology
- Evidence-based reporting
- Control effectiveness validation
- Risk-based prioritization
- Audit-ready documentation
Conclusion
Cloud, API, and Zero Trust environments have redefined how organizations build and secure systems. Attackers no longer rely on exploiting software vulnerabilities alone—they abuse identities, permissions, trust relationships, and business logic. Traditional penetration testing approaches are insufficient in this new threat landscape.
Modern Penetration Testing Services must simulate real attacker behavior across cloud infrastructure, APIs, and Zero Trust architectures. By identifying realistic attack paths and validating security assumptions, organizations can reduce breach risk, strengthen security posture, and ensure their controls work as intended.
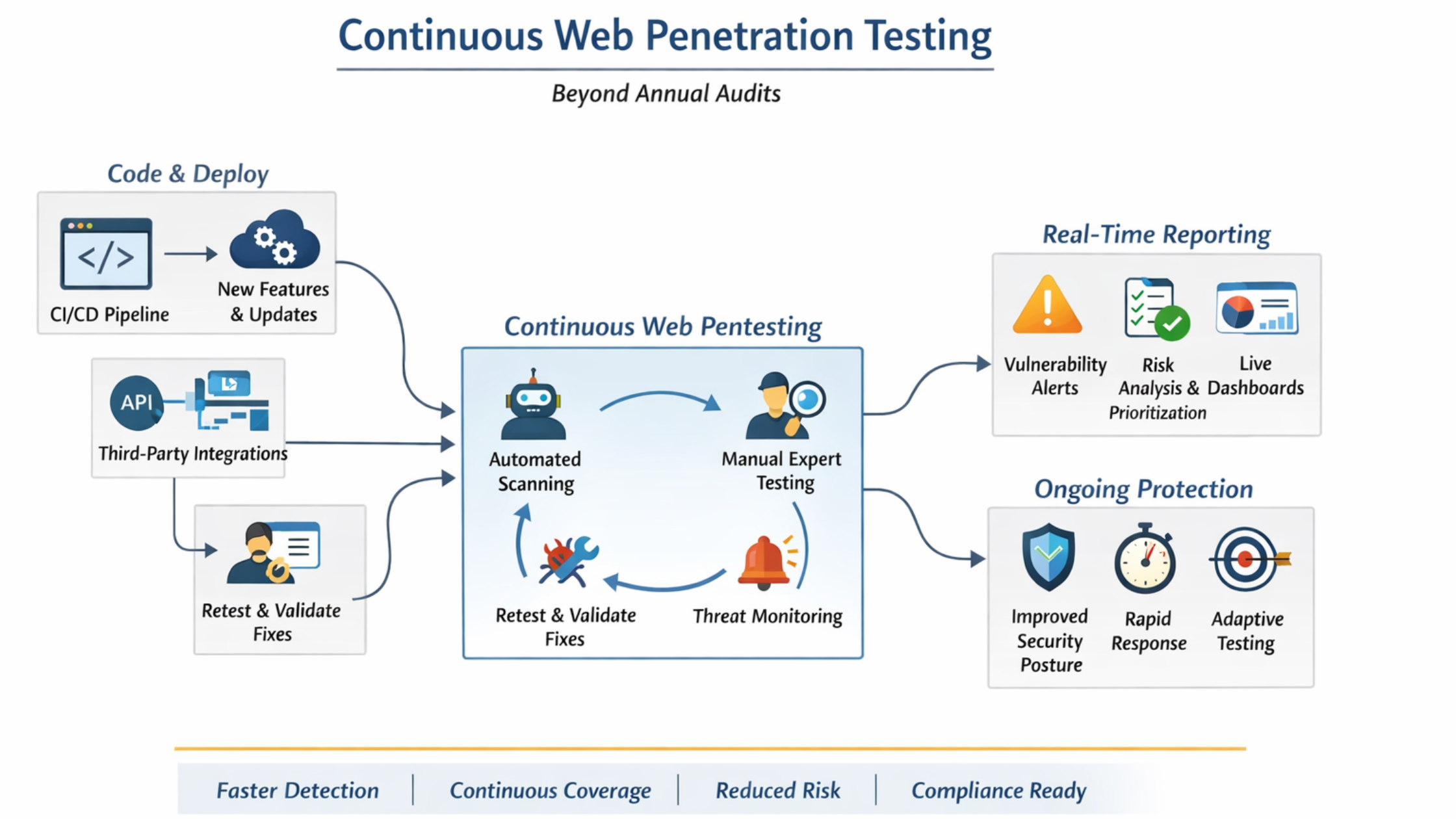
Penetration testing is no longer a periodic exercise. It is a critical capability for any organization operating modern, distributed, identity-driven systems.