Continuous Web Penetration Testing: Why Businesses Need It Instead of Annual Audits
Modern websites are no longer static assets updated once or twice a year. In 2026, most businesses deploy new features, APIs, integrations, and cloud changes continuously. While development has evolved, security testing in many organizations still relies on annual web penetration audits—a model that creates long periods of unseen risk.
Continuous web penetration testing addresses this gap by validating website security throughout the year, ensuring vulnerabilities are discovered as they appear, not months later.
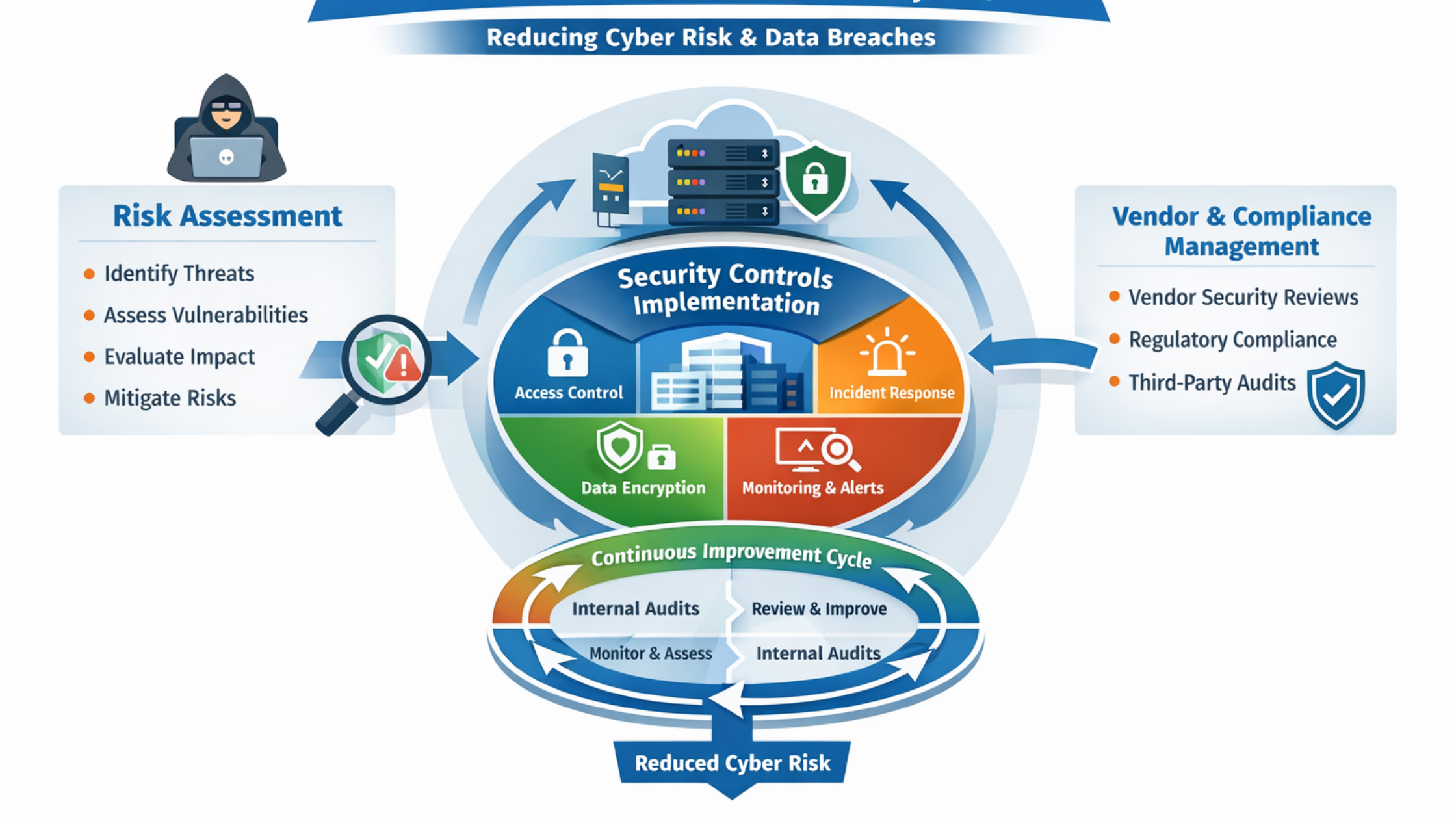
Why Annual Web Penetration Testing Falls Short
Annual penetration tests provide a one-time assessment of a website’s security posture. Once completed, the environment immediately starts changing—often invalidating the results.
Key issues with annual audits include:
- Security findings become outdated quickly as new code is deployed
- Vulnerabilities introduced after the audit remain undetected
- Third-party integrations and plugins are rarely re-tested
- Attackers exploit changes long before the next scheduled test
- Focus is often on compliance rather than real-world risk
In fast-moving environments, this creates long exposure windows that attackers actively exploit.
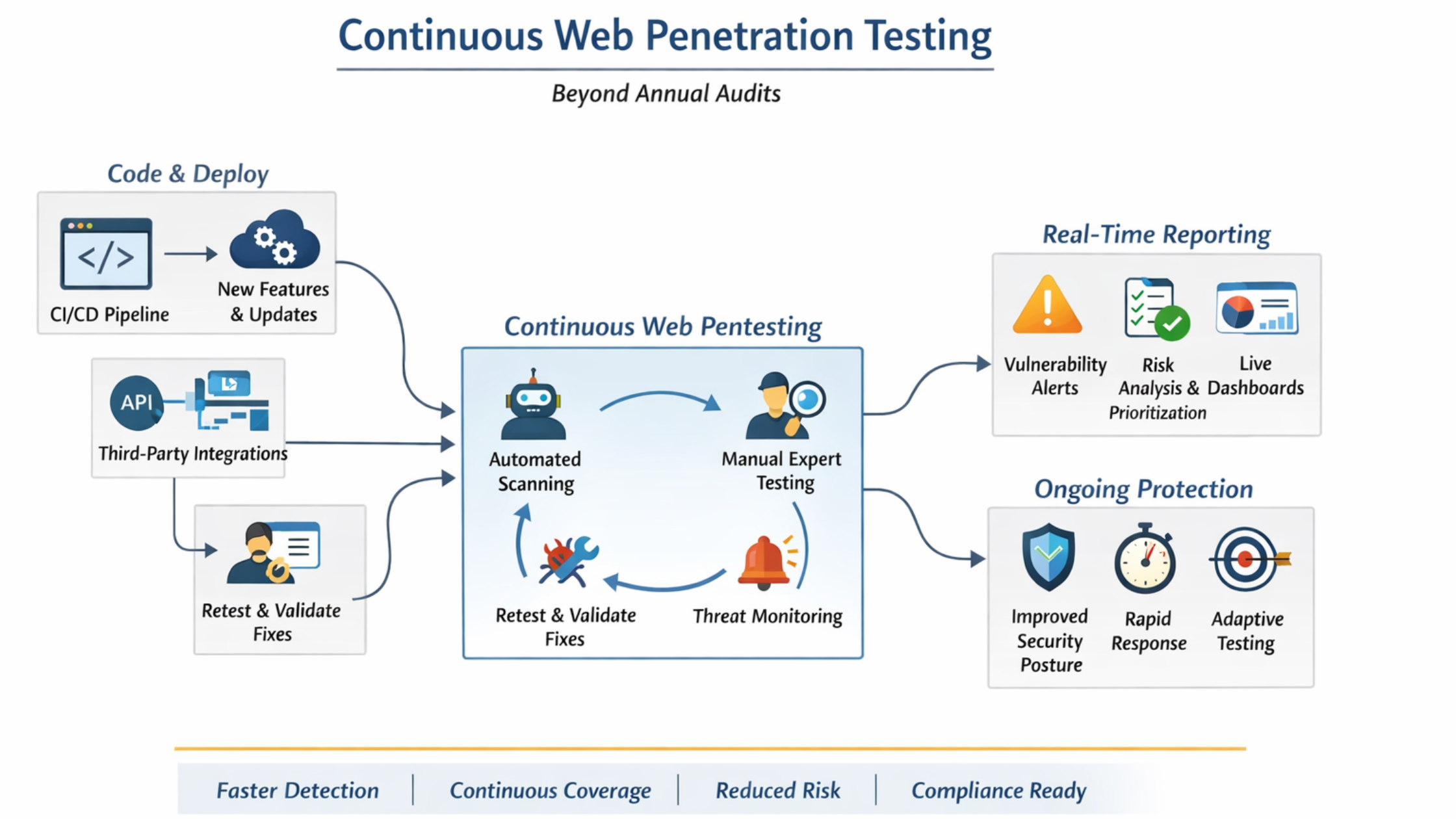
What Continuous Web Penetration Testing Really Means
Continuous web penetration testing is an ongoing security practice that evaluates websites whenever meaningful changes occur. It combines automation with expert-led testing to ensure both speed and accuracy.
This approach focuses on:
- Testing new features and updates as they are released
- Re-validating security controls after fixes and deployments
- Monitoring evolving attack techniques
- Prioritizing vulnerabilities based on business impact
Rather than a static report, businesses gain continuous security visibility.
How Continuous Web Penetration Testing Works in Practice
Continuous testing is not about running scanners repeatedly. It involves a structured and controlled process.
Typically, it includes:
- Automated detection of new endpoints, APIs, and parameters
- Manual exploitation to confirm real attack paths
- Regular re-testing after code changes or infrastructure updates
- Ongoing risk scoring and reporting
- Collaboration with development and security teams
This ensures findings are accurate, relevant, and actionable.
Why Businesses Are Moving Away From Annual Audits
Faster Identification of High-Risk Vulnerabilities
Continuous testing shortens the time between vulnerability introduction and detection, significantly reducing attack opportunities.
Alignment With Agile and DevOps Workflows
As development becomes faster, security testing must keep pace. Continuous testing integrates naturally into CI/CD pipelines.
Reduced Breach Exposure
When vulnerabilities are discovered early, attackers have less time to exploit them in real-world scenarios.
Smarter Risk Prioritization
Findings are evaluated based on exploitability and business impact, not just severity scores.
Always-Ready Compliance Posture
Instead of scrambling before audits, organizations maintain a consistent level of security assurance throughout the year.
Continuous Web Penetration Testing and CI/CD Pipelines
Security testing is increasingly shifting left into the development lifecycle.
Continuous penetration testing supports:
- Pre-production testing for new website features
- API security testing during build stages
- Post-deployment attack simulation
- Ongoing validation of authentication, authorization, and session management
This approach prevents insecure code from reaching production environments.
Vulnerabilities Commonly Discovered Through Continuous Testing
Ongoing testing often uncovers issues that appear after annual audits are completed, such as:
- Authentication flaws introduced during feature updates
- Broken access controls in APIs
- Business logic weaknesses in workflows
- Client-side security issues in modern JavaScript frameworks
- Cloud configuration errors affecting web security
These vulnerabilities frequently emerge between major releases.
Who Benefits Most From Continuous Web Penetration Testing
Continuous testing is especially valuable for:
- SaaS platforms with frequent deployments
- E-commerce websites handling sensitive transactions
- Fintech and healthcare portals
- Organizations using third-party APIs and services
- Cloud-native and microservices-based applications
For these businesses, annual testing alone leaves too many blind spots.
Addressing Common Challenges
Some organizations hesitate due to concerns around cost, alert fatigue, or false positives.
Modern continuous testing models address this by:
- Combining automation with expert validation
- Offering flexible testing scopes
- Providing clear, risk-based reporting
- Delivering testing through scalable PTaaS platforms
This makes continuous testing practical and manageable.
The Future of Website Security Testing
As websites become more dynamic and interconnected, continuous penetration testing is becoming the standard. Annual audits may still support compliance, but they are no longer sufficient for real security assurance.
Security must evolve at the same speed as development.
Conclusion
Continuous web penetration testing provides real-time security validation for modern websites, reducing risk and improving resilience. Unlike annual audits, it adapts to change, detects vulnerabilities early, and aligns with how businesses build and operate today.
For organizations serious about protecting their websites, continuous testing is no longer a luxury—it is a necessity.