Why ISO 27001 Certification Services Are Critical for Reducing Cyber Risk
Cyber risks and data breaches are no longer rare incidents limited to large enterprises or tech companies. Today, organizations of all sizes face constant threats such as ransomware attacks, phishing campaigns, insider misuse, cloud misconfigurations, and supply-chain vulnerabilities. A single data breach can result in financial losses, regulatory penalties, operational downtime, reputational damage, and loss of customer trust.
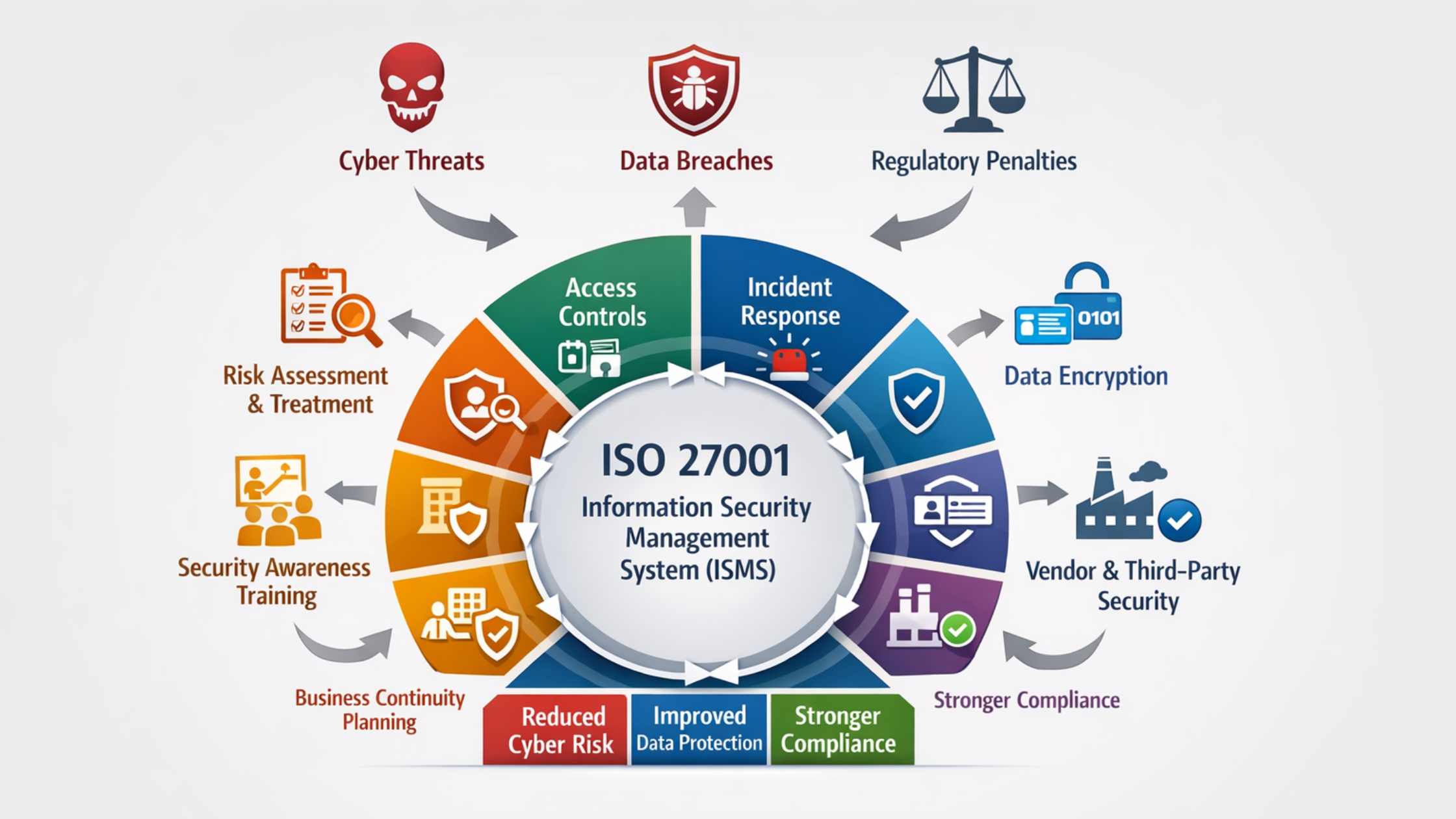
Many businesses invest in security tools like firewalls, antivirus software, or monitoring systems, yet still suffer breaches because security efforts are often unstructured and reactive. This is where ISO 27001 certification services play a critical role. ISO 27001 provides a globally recognized, systematic, and risk-based framework for managing information security. Instead of focusing only on technology, it addresses people, processes, and policies together through an Information Security Management System (ISMS).
By implementing ISO 27001, organizations move from reacting to cyber incidents to proactively identifying, assessing, and reducing cyber risks before they lead to data breaches.
Key takeaways from the introduction:
- Cyber risk impacts business continuity and brand reputation
- Security tools alone are not enough to prevent breaches
- ISO 27001 certification services offer a structured and preventive approach
- Focuses on people, process, and technology together
Understanding ISO 27001 and Its Role in Cyber Risk Reduction
ISO 27001 is an international standard developed to help organizations establish, implement, maintain, and continually improve an Information Security Management System. The standard is designed to protect the confidentiality, integrity, and availability of information assets. Unlike one-time security controls, ISO 27001 emphasizes continuous risk management and improvement.
ISO 27001 certification services guide organizations in identifying their critical information assets, assessing threats and vulnerabilities, and applying appropriate security controls based on risk. This ensures that security efforts are aligned with real business risks rather than assumptions.
By following ISO 27001, organizations create a security culture where cyber risk management becomes part of daily operations rather than a checklist activity.
How ISO 27001 supports cyber risk reduction:
- Focuses on risk assessment instead of generic controls
- Covers physical, technical, and organizational security
- Encourages continuous monitoring and improvement
- Aligns security with business objectives
Risk-Based Approach: The Foundation of ISO 27001 Security
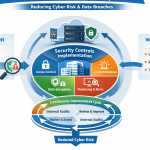
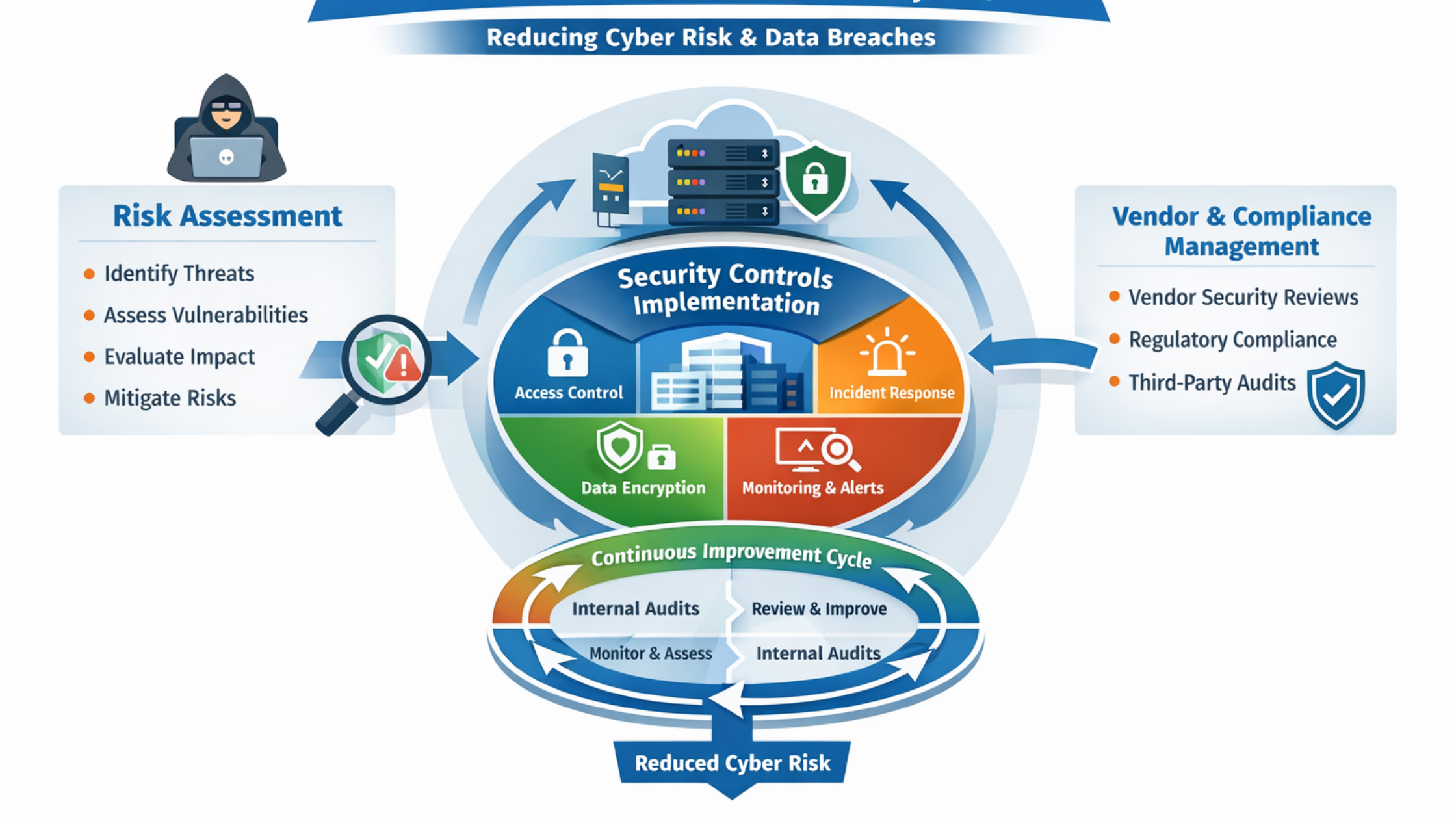
At the core of ISO 27001 is a risk-based approach to information security. Instead of applying the same controls everywhere, organizations are required to identify risks specific to their environment. This includes understanding what information assets they have, what threats could affect them, and how severe the impact would be if a breach occurs.
ISO 27001 certification services help organizations conduct structured risk assessments that highlight vulnerabilities before attackers exploit them. By addressing high-risk areas first, businesses significantly reduce the likelihood of successful cyberattacks.
This approach ensures that security investments are targeted, effective, and aligned with real business priorities.
Risk-based security benefits:
- Early identification of cyber threats and vulnerabilities
- Prioritization of high-impact risks
- Reduced exposure to known attack vectors
- Smarter allocation of security budgets
Strong Access Control to Prevent Unauthorized Data Access
Unauthorized access is one of the most common causes of data breaches. Weak passwords, shared accounts, excessive privileges, and poor user management often allow attackers or insiders to access sensitive data.
ISO 27001 enforces strict access control policies to ensure that only authorized individuals can access information based on their job roles. Through ISO 27001 certification services, organizations implement the principle of least privilege, ensuring users have only the access they need and nothing more.
This significantly reduces the risk of data leaks, insider threats, and credential misuse.
How access control reduces breaches:
- Role-based access management
- Least privilege enforcement
- Secure user onboarding and offboarding
- Reduced insider and credential-based attacks
Incident Management and Faster Breach Response
No organization can guarantee that a cyber incident will never occur. What matters most is how quickly and effectively the organization responds. ISO 27001 requires organizations to establish incident response procedures before an incident happens.
With ISO 27001 certification services, businesses define roles, responsibilities, escalation paths, and communication processes for handling security incidents. This preparedness ensures that incidents are detected early and contained quickly, reducing damage.
A fast and coordinated response can mean the difference between a minor security event and a major data breach.
Incident management advantages:
- Faster detection of security incidents
- Reduced downtime and operational impact
- Minimized data loss
- Clear response roles and accountability
Data Protection Through Classification and Encryption
Data breaches often occur because sensitive information is not properly protected. ISO 27001 requires organizations to classify data based on sensitivity and apply appropriate security controls.
ISO 27001 certification services help organizations define data handling rules, encryption requirements, secure storage, and backup strategies. Even if attackers gain access to systems, encrypted and properly managed data remains unreadable and unusable.
This significantly reduces the impact of breaches and protects critical business and customer data.
Data protection benefits under ISO 27001:
- Data classification based on sensitivity
- Encryption for data at rest and in transit
- Secure backup and recovery processes
- Reduced impact of ransomware and data theft
Reducing Human Error Through Security Awareness
Human error remains one of the biggest contributors to cyber incidents. Phishing emails, weak passwords, accidental data sharing, and lack of awareness often open the door for attackers.
ISO 27001 emphasizes regular security awareness and training programs for employees. Through ISO 27001 certification services, organizations educate staff on recognizing threats, following security policies, and handling data responsibly.
A well-trained workforce acts as a strong first line of defense against cyber threats.
Human risk reduction outcomes:
- Lower success rate of phishing attacks
- Improved password hygiene
- Safer data handling practices
- Stronger security culture across the organization
Continuous Monitoring and Improvement Against Evolving Threats
Cyber threats are constantly evolving, and security controls that worked yesterday may not be effective tomorrow. ISO 27001 addresses this by requiring continuous monitoring, internal audits, and management reviews.
ISO 27001 certification services ensure that organizations regularly review their risks, controls, and security performance. This allows businesses to adapt quickly to new threats, technologies, and regulatory changes.
Continuous improvement ensures that security does not become outdated or ineffective.
Continuous improvement benefits:
- Early detection of control weaknesses
- Regular updates to risk assessments
- Improved long-term security posture
- Better readiness for emerging threats
Managing Third-Party and Supply Chain Cyber Risks
Many high-profile data breaches originate from third-party vendors rather than the organization itself. ISO 27001 requires businesses to assess and manage supplier and partner risks.
Through ISO 27001 certification services, organizations implement vendor security assessments, contractual security requirements, and ongoing monitoring of third-party risks.
This reduces exposure to supply-chain attacks and ensures that partners meet minimum security standards.
Third-party risk management advantages:
- Reduced supply-chain attack risks
- Improved vendor accountability
- Clear security expectations for partners
- Stronger overall security ecosystem
Alignment With Regulatory and Compliance Requirements
ISO 27001 aligns well with multiple regulatory and compliance frameworks such as the DPDP Act 2023, GDPR, PCI DSS, HIPAA, and SOC 2. This alignment helps organizations meet legal requirements while strengthening security controls.
ISO 27001 certification services simplify compliance efforts by creating a single security framework that supports multiple regulations. Strong compliance reduces the risk of fines, legal action, and reputational damage.
Compliance and security benefits:
- Reduced regulatory penalties
- Improved audit readiness
- Simplified compliance management
- Enhanced trust from customers and regulators
Business Continuity and Reduced Impact of Cyber Incidents
Cyber incidents often disrupt business operations. ISO 27001 integrates business continuity and disaster recovery planning into information security management.
By working with ISO 27001 certification services, organizations prepare for system failures, cyberattacks, and data loss scenarios. This ensures critical operations can continue even during security incidents.
Strong resilience reduces both financial losses and customer dissatisfaction.
Business continuity benefits:
- Faster recovery from cyber incidents
- Reduced operational downtime
- Protection of critical services
- Improved organizational resilience
Conclusion: ISO 27001 Certification Services as a Long-Term Cybersecurity Strategy
ISO 27001 is far more than a compliance requirement—it is a strategic framework for reducing cyber risk and preventing data breaches. By focusing on risk-based security, access control, incident preparedness, employee awareness, and continuous improvement, ISO 27001 helps organizations build strong cyber resilience.
Organizations that invest in ISO 27001 certification services move from reactive security to proactive risk management. This not only reduces the likelihood of data breaches but also strengthens customer trust, regulatory compliance, and long-term business sustainability.
In a world where cyber threats are inevitable, ISO 27001 provides the structure, discipline, and confidence businesses need to stay secure.