Understanding Cloud Security Assessment Frameworks
As businesses increasingly rely on cloud services to store and manage their data, ensuring the security of these environments becomes paramount. Cloud Security Assessment services have become a crucial component in safeguarding cloud infrastructure against potential threats and vulnerabilities. This
How to Implement Information Security Management for HIPAA Compliance
Information Security Management is crucial for organizations that handle sensitive health information. Implementing robust Information Security Management practices ensures the confidentiality, integrity, and availability of this data, which is essential for HIPAA compliance. HIPAA, the Health Insurance Portability and Accountability
How to Prepare for an SSAE 18 Audit
In today’s fast-paced business environment, ensuring the security and integrity of your organization’s data is crucial. One way to achieve this is by obtaining an SSAE 18 report, which shows your commitment to maintaining high standards of internal controls. Preparing
Cost-Effective Ways to Enhance Information Security
In today's digital age, protecting sensitive information is crucial for businesses of all sizes. While large enterprises may have extensive resources to invest in robust security measures, smaller businesses often struggle to balance the need for strong information security with
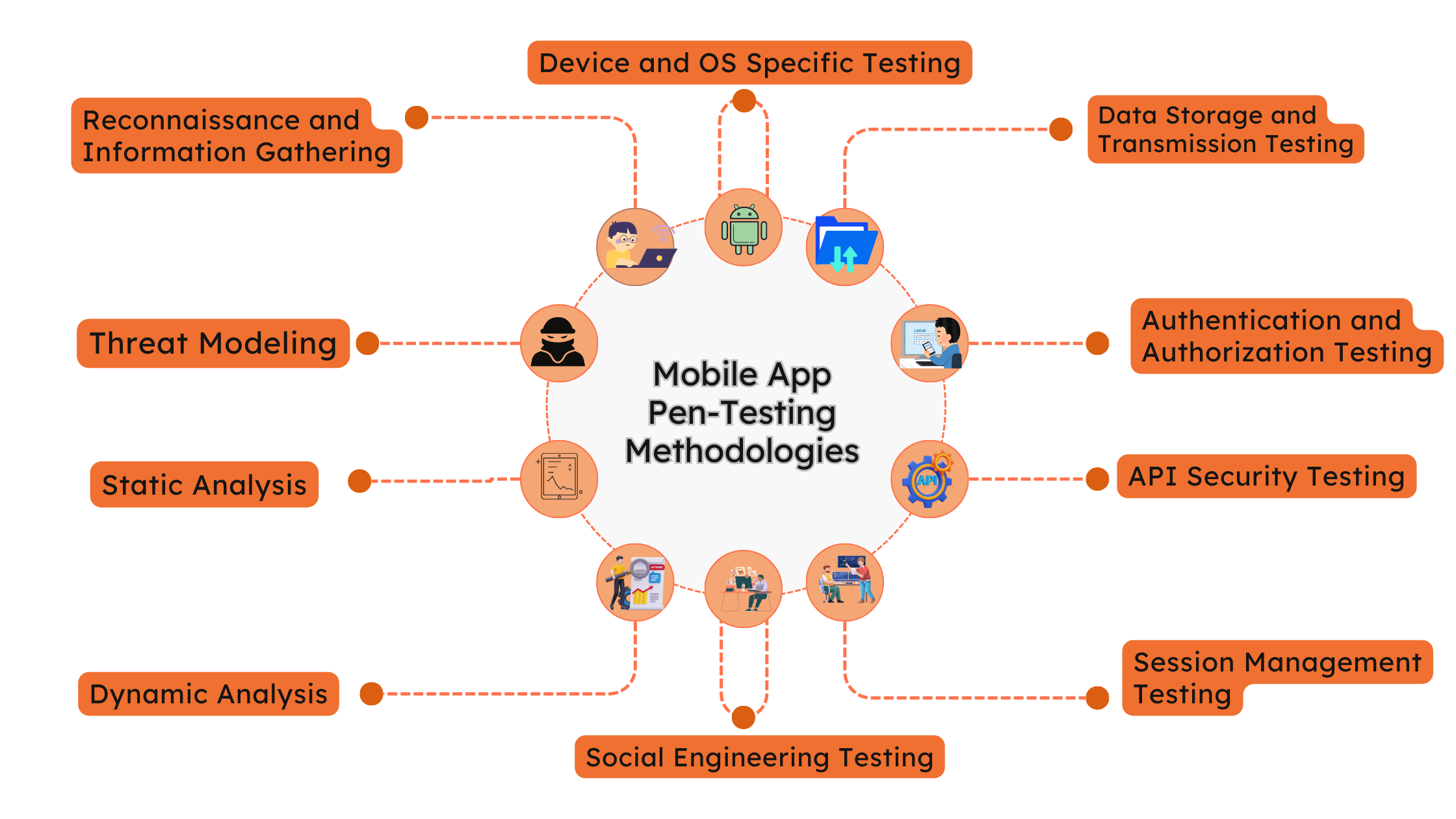
Exploring Mobile App Pen-Testing Methodologies for Secure Mobile App Development
In today's digital age, healthcare organizations handle vast amounts of sensitive data, from patient medical records to financial information. Protecting this data is not only a legal requirement but also a crucial aspect of maintaining trust and operational integrity. This
Understanding ISO 27001 Certification for Healthcare Organizations
In today's digital age, healthcare organizations handle vast amounts of sensitive data, from patient medical records to financial information. Protecting this data is not only a legal requirement but also a crucial aspect of maintaining trust and operational integrity. This
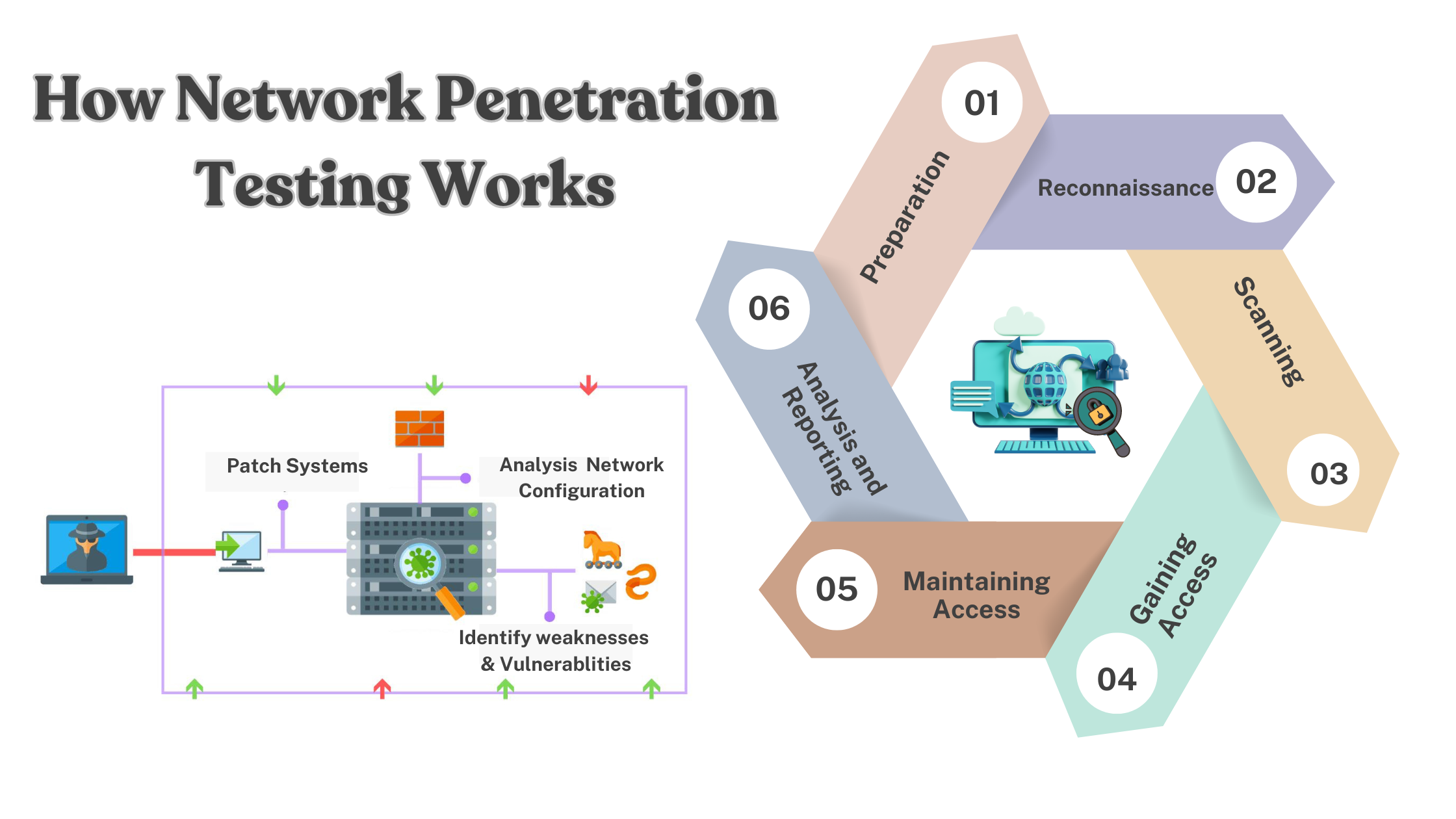
How Network Penetration Testing Works
In today's digital age, information security services are paramount for businesses to protect their sensitive data and systems from cyber threats. One of the crucial aspects of information security is Network Penetration Testing. This practice involves simulating cyber attacks to
How to Perform Mobile Application Penetration Testing
In today's digital landscape, mobile applications have become an integral part of our daily lives, facilitating everything from banking to social networking. As their usage increases, so does the need for robust security measures to protect sensitive user data. This
Understanding PCI DSS Compliance: A Business Guide
In today's digital age, ensuring the security of sensitive financial information is paramount for businesses. One of the key frameworks that governs this security is the Payment Card Industry Data Security Standard (PCI DSS). This standard is designed to protect
Navigating the Path to ISO 27001 Certification Services: A Comprehensive Guide
In the digital age, where data is the new currency, safeguarding information assets is paramount for businesses worldwide. ISO 27001, the international standard for Information Security Management Systems (ISMS), provides a robust framework for organizations to establish, implement, maintain, and