How PCI Compliance Consulting Services Help Prevent Costly Data Breaches
The Payment Card Industry Data Security Standard (PCI DSS) has evolved into one of the most rigorous security frameworks globally. With PCI DSS v4.0 now in effect, compliance is no longer about checking boxes—it’s about implementing adaptive, risk-based security controls. Many businesses, especially those handling high-volume transactions, struggle to interpret the technical requirements, align them with their infrastructure, and validate them through audits.
This is where PCI Compliance Consulting Services provide real value. By going beyond surface-level compliance, consultants translate the technical language of PCI DSS into secure architecture, enforceable policies, and automated controls that directly reduce breach risk.
1. Network Segmentation and Architecture Hardening
One of the most effective breach-prevention strategies is reducing the PCI scope through network segmentation.
- Micro-Segmentation: Consultants implement VLAN-based or software-defined segmentation (SDN) to isolate cardholder data environments (CDE) from non-sensitive workloads. This reduces the attack surface significantly.
- Firewall Rule Optimization: PCI DSS requires restricting inbound/outbound traffic. Consultants analyze existing firewall ACLs, identify overly permissive rules (e.g., ANY-ANY), and apply least-privilege rulesets.
- Zero Trust Principles: Instead of flat networks, PCI experts design architectures that assume breach and validate every connection using identity-based policies.
This architectural redesign ensures that even if an attacker compromises one system, lateral movement toward the CDE is nearly impossible.
2. Advanced Encryption and Key Management
Encryption isn’t just about enabling TLS—PCI DSS mandates strong cryptography with proper key lifecycle management.
PCI Compliance Consulting Services help businesses implement:
- Point-to-Point Encryption (P2PE) for payment terminals, so card data is encrypted immediately at swipe/dip.
- Tokenization: Consultants integrate tokenization solutions where PAN (Primary Account Number) values are replaced with non-sensitive tokens.
- Hardware Security Modules (HSMs): Consultants design and configure centralized HSMs for key generation, rotation, and destruction, meeting FIPS 140-2 standards.
- TLS 1.2/1.3 Enforcement: Legacy SSL/TLS protocols are removed, with secure cipher suites configured across load balancers, APIs, and web servers.
Improper encryption and weak key management are common breach vectors—consultants ensure they are technically airtight.
3. Secure Software Development and Code Review
With PCI DSS v4.0, Requirement 6.3.2 mandates secure coding practices. Consulting services dive deep into DevSecOps pipelines:
- Static Application Security Testing (SAST): Automated scans detect vulnerabilities like SQL injection or buffer overflows in custom payment applications.
- Dynamic Application Security Testing (DAST): Web applications are tested in runtime against OWASP Top 10 threats.
- Software Composition Analysis (SCA): Detects open-source library vulnerabilities and license risks.
- Secure SDLC Policies: Consultants integrate code review gates and commit hooks in Git repositories to enforce compliance.
This approach not only ensures PCI DSS compliance but also proactively reduces exploitable flaws in payment software.
4. Continuous Vulnerability Management
PCI DSS requires quarterly scans, but consultants elevate this by embedding vulnerability management into CI/CD workflows.
- Credentialed Scanning with tools like Nessus or Qualys for in-depth system visibility.
- Patch Management Automation: Integrating WSUS, SCCM, or Ansible-based patching pipelines to reduce exposure windows.
- Threat-Driven Prioritization: Consultants map CVEs to real-world exploitability (using EPSS or CISA KEV lists) to prioritize remediation.
- Container Security: For modern environments, they scan Docker/Kubernetes images for misconfigurations and vulnerabilities.
This proactive approach reduces the average time-to-remediate (TTR), which directly correlates with breach prevention.
5. Identity and Access Management (IAM)
Mismanaged credentials are among the top causes of breaches. PCI Compliance Consulting Services implement:
- Privileged Access Management (PAM) tools to enforce just-in-time access for admins.
- Multi-Factor Authentication (MFA) across all CDE access points.
- Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) policies.
- Credential Vaulting: Centralized rotation of service account credentials using solutions like HashiCorp Vault or CyberArk.
These technical controls minimize insider threats and credential theft attacks.
6. Security Information and Event Management (SIEM) Integration
PCI DSS requires log monitoring and retention (Requirement 10). Consultants integrate SIEM platforms such as Splunk, ELK, or QRadar to provide:
- Centralized Log Aggregation from firewalls, IDS/IPS, databases, and applications.
- Real-Time Correlation Rules to detect anomalies like brute-force attempts or privilege escalation.
- UEBA (User and Entity Behavior Analytics) to detect insider misuse or compromised accounts.
- Immutable Log Storage for forensic readiness, often backed by WORM (Write Once Read Many) storage.
Without real-time monitoring, a breach could go undetected for months. Consultants ensure organizations achieve mean-time-to-detect (MTTD) in hours, not weeks.
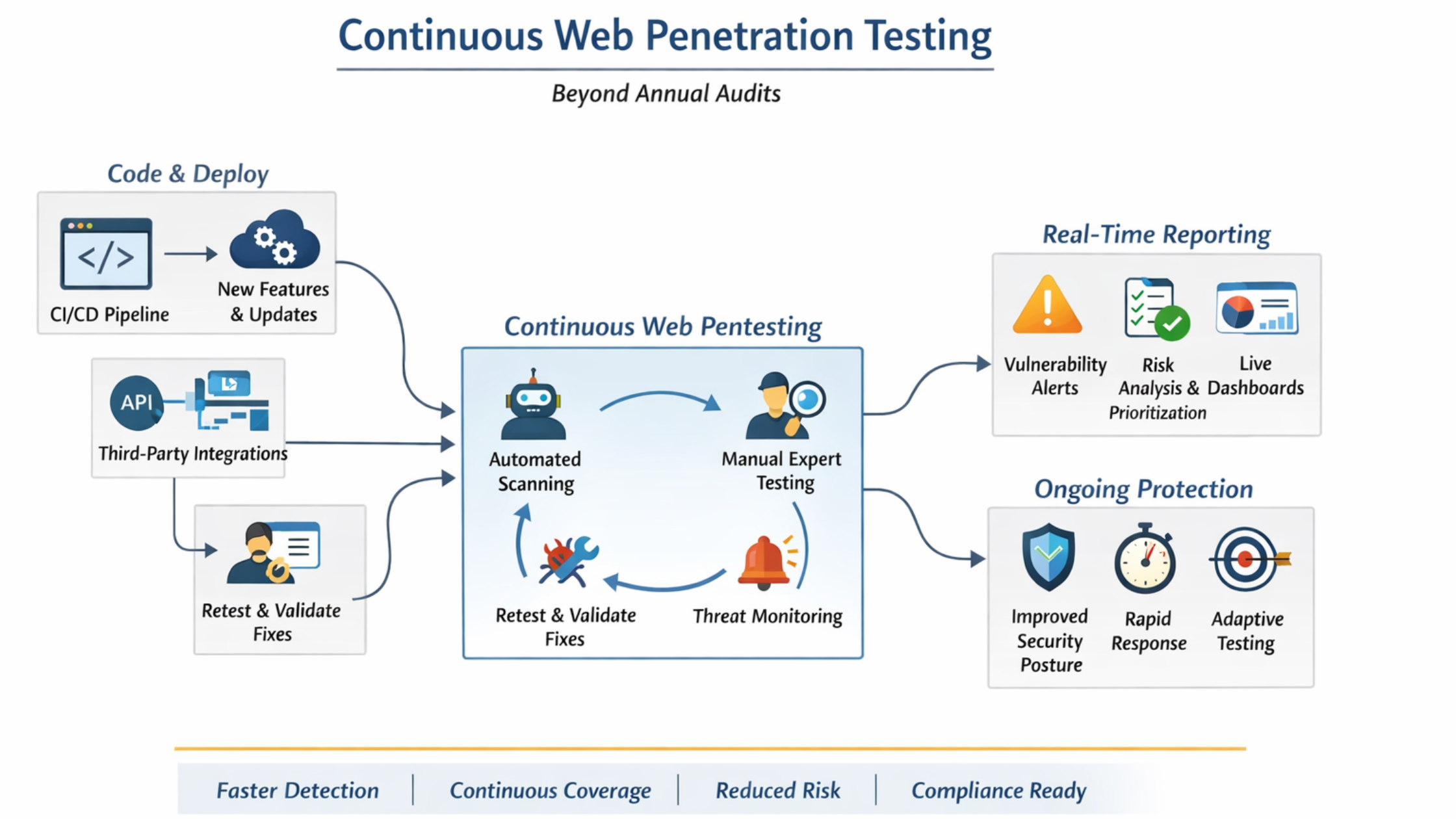
7. Penetration Testing and Red Team Exercises
Beyond required annual pen tests, consultants orchestrate advanced adversary simulations:
- Red Team Engagements: Simulate APT-style attacks targeting the CDE.
- Purple Team Exercises: Combine offensive and defensive teams to improve detection capabilities.
- API Security Testing: Given the rise of payment APIs, consultants focus on authentication flaws, improper rate limiting, and business logic vulnerabilities.
- Social Engineering: Testing employee awareness against phishing and vishing, as per PCI DSS guidance.
This real-world testing validates not just compliance but resilience against evolving attack vectors.
8. Incident Response and Forensics Readiness
Consultants develop playbooks tailored to PCI breaches:
- Forensic Imaging: Ensuring systems can be captured without tampering with evidence.
- Chain of Custody Procedures for legal defensibility.
- Tabletop Exercises simulating breaches to test readiness.
- Integration with SOAR platforms to automate containment (e.g., disabling compromised accounts, isolating infected hosts).
A well-prepared incident response plan drastically reduces breach impact.
9. Continuous Compliance Monitoring
Instead of treating PCI as a yearly audit, consultants deploy compliance-as-code frameworks:
- Automated Policy Validation: Using tools like Chef InSpec or OpenSCAP to continuously check systems against PCI controls.
- Drift Detection: Alerting if firewall rules, encryption configs, or IAM settings deviate from compliance baselines.
- Dashboards for Executives and Auditors: Real-time compliance scorecards tied to KPIs.
This continuous model ensures that compliance is sustained, not just achieved.
Conclusion
While PCI DSS sets the baseline, PCI Compliance Consulting Services provide the technical expertise to go beyond checklist compliance and build resilient security architectures. From segmentation and encryption to SIEM integration and DevSecOps, consultants close the gaps that attackers exploit.
By embedding technical controls, automating compliance, and validating through real-world testing, PCI consultants in Sheridan, WY help organizations prevent costly data breaches that could cripple finances and reputation.
For businesses handling payment card data, working with PCI Compliance Consulting Services is no longer optional—it’s a strategic necessity for both compliance and cyber resilience.