The Role of PCI DSS Consulting Services in Tokenization & Encryption Strategies
As payment environments become more distributed—spanning cloud platforms, APIs, mobile apps, CI/CD pipelines, and third-party services—protecting cardholder data is no longer just about “encrypting the database.” Modern PCI DSS compliance depends on how encryption and tokenization are designed, implemented, governed,
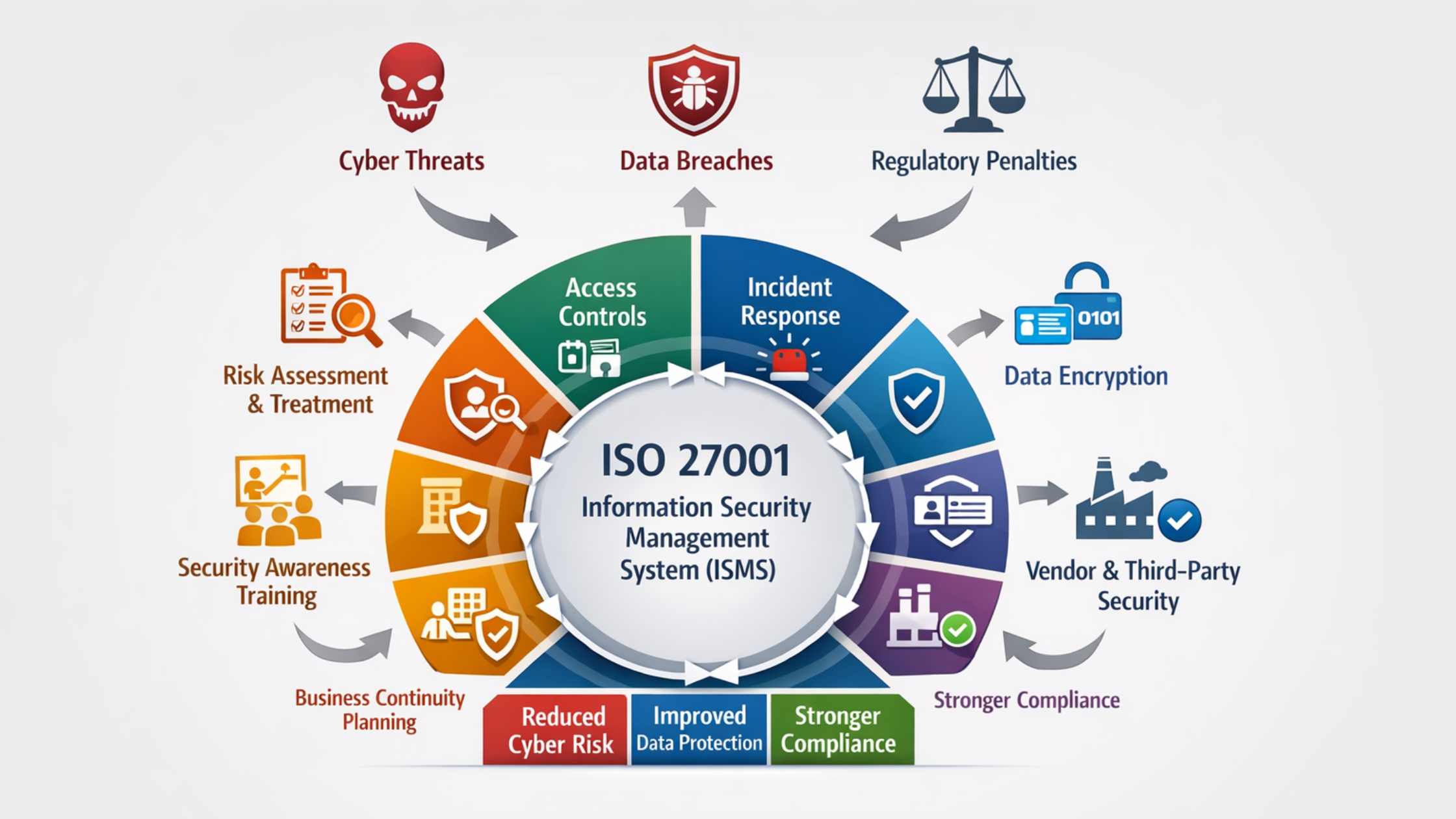
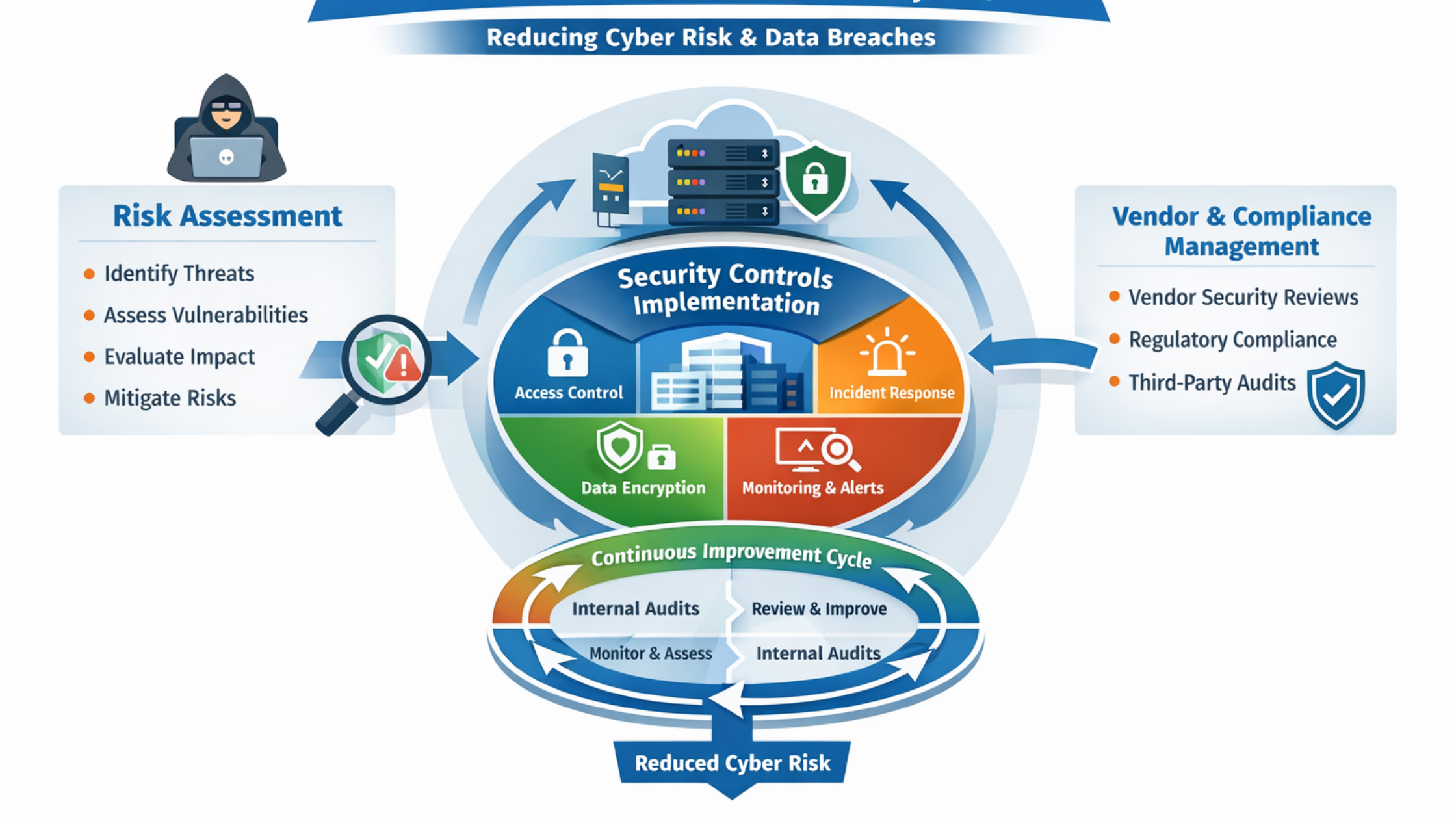
Why ISO 27001 Certification Services Are Critical for Reducing Cyber Risk
Cyber risks and data breaches are no longer rare incidents limited to large enterprises or tech companies. Today, organizations of all sizes face constant threats such as ransomware attacks, phishing campaigns, insider misuse, cloud misconfigurations, and supply-chain vulnerabilities. A single
How ISO 27001 Certification Services Reduce Cyber Risk and Data Breaches
In today’s digital world, cyberattacks are no longer rare events. Businesses of all sizes—startups, SMEs, and large enterprises—face constant threats such as ransomware, phishing, insider attacks, and data leaks. Firewalls, antivirus software, and cloud security tools are important, but they
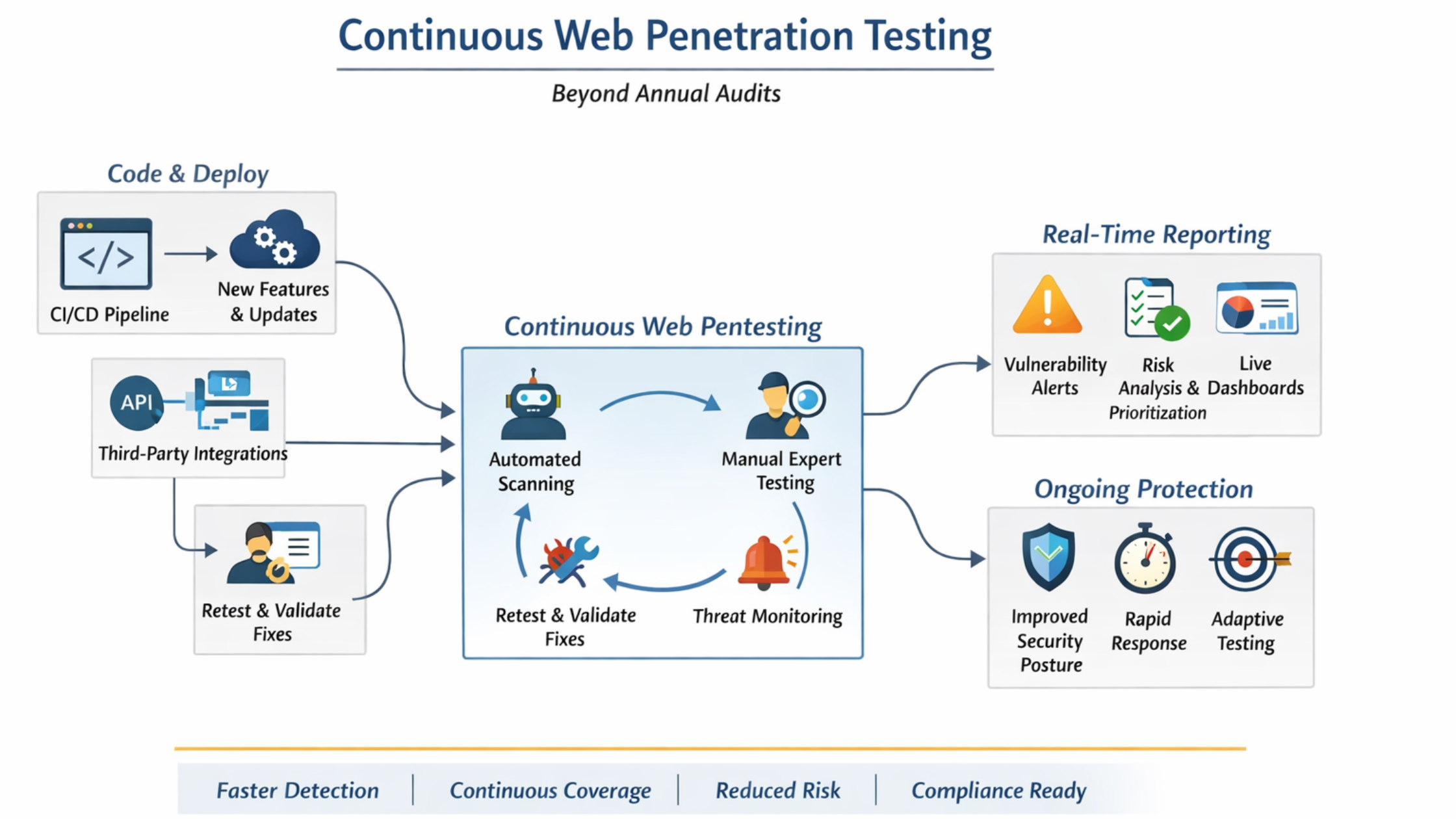
Continuous Web Penetration Testing: Why Businesses Need It Instead of Annual Audits
Modern websites are no longer static assets updated once or twice a year. In 2026, most businesses deploy new features, APIs, integrations, and cloud changes continuously. While development has evolved, security testing in many organizations still relies on annual web
Why Businesses Are Shifting to Managed Information Security Services in 2026
In 2026, cyber threats are no longer occasional incidents—they are constant, intelligent, and highly automated. Businesses of all sizes are facing ransomware attacks, data breaches, compliance failures, and supply-chain risks at an unprecedented scale. Traditional, in-house security models are struggling
Penetration Testing Services for Cloud, API & Zero Trust Environments
Modern enterprise environments are no longer defined by a clear network perimeter. Cloud platforms, API-driven architectures, and Zero Trust security models have fundamentally changed how systems are built and accessed. While these architectures improve scalability and agility, they also introduce
How GDPR Consultant Services Help Ensure AI Data Processing Compliance
Artificial Intelligence (AI) is transforming how businesses collect, analyze, and use data. From chatbots and recommendation engines to fraud detection and predictive analytics, AI systems depend heavily on personal data. While AI brings efficiency and innovation, it also creates serious
How Vulnerability Assessment Services Strengthen Cybersecurity Posture
In today’s digital world, businesses depend heavily on technology, networks, and data-driven systems. However, with this dependence comes the growing threat of cyberattacks. Every organization, regardless of size or industry, faces risks from vulnerabilities—weak points in software, systems, or configurations
The Role of GDPR Consultant Services in Managing Data Breaches Effectively
In today’s digital age, data is one of the most valuable assets for businesses. However, with increasing reliance on technology, the risk of data breaches has never been higher. Personal data mishandling or unauthorized access can not only damage a
How Cloud-Based Solutions Impact PCI DSS Compliance Services in 2025
In 2025, businesses handling payment card data face higher scrutiny and more complex compliance requirements. PCI DSS Compliance Services are now more critical than ever—not only to meet regulatory standards but also to maintain customer trust, protect sensitive information, and